Harbor is a corporate registry of containers. Currently, VMware uses Harbor in its container management products: vSphere Integrated Containers (VIC) and Pivotal Container Service (PKS), in addition, you can install it and use it separately. Since management through a graphical interface does not allow automating work, we will get acquainted with managing Harbor through the REST API.

It is best to start your acquaintance with the REST API at the Harbor home page: https://goharbor.io/ and the github page: https://github.com/goharbor/harbor . To explore all available REST API functions and their parameters, download the file https://github.com/goharbor/harbor/blob/master/docs/swagger.yaml . Swagger is a framework for describing REST APIs. The swagger.yaml file can be opened in the online editor http://editor.swagger.io/ or import it into Postman (in this case, I recommend replacing localhost with the name of your harbor server in the line “host: localhost”: for example, “host: harbor.zabedu.ru”). The image on the right is the beginning of the list of commands loaded into Postmap. A total of 106 query templates were imported (Harbor version 1.7.0).
List of public projects
It’s time to make your first request. Need a complete list of projects on the Harbor server? In the list of imported queries, in the “projects” section, select the “List projects” query. The complete query looks like this: The variable names are specified in curly braces in Postman, you need to set their values before running the query. Another way of specifying variables is possible, you can put a colon (:) in front of the variable name.
https://harbor.zabedu.ru/api/projects?name={{name}}&public={{public}}&owner={{owner}}&page={{page}}&page_size={{page_size}}Remove all additional conditions from the request, since you do not have the required values yet.
https://harbor.zabedu.ru/api/projects
Send a request to the server – Send …
[
{
"project_id": 121,
"owner_id": 3,
"name": "zabedu",
"creation_time": "2018-12-20T10:11:10Z",
"update_time": "2018-12-20T10:11:10Z",
"deleted": false,
"owner_name": "",
"togglable": false,
"current_user_role_id": 0,
"repo_count": 2,
"metadata": {
"auto_scan": "true",
"enable_content_trust": "true",
"prevent_vul": "true",
"public": "true",
"severity": "low"
}
}
]
If a response is not received, then check the server’s operation and its availability over the network; to check, you can enter a request in the address bar of the browser or call it via curl:
$ curl -i -k -X GET "https://harbor.zabedu.ru/api/projects"
This is a simple GET request, without authorization, it returns a list of public projects only. After adding authorization parameters, the request will display a list of all projects available to you.
Authorization
To configure authorization on the Authorization tab, select the Basic type, specify the username, password and click Preview Request, authorization parameters will be added to the list of request headers (Headers tab).
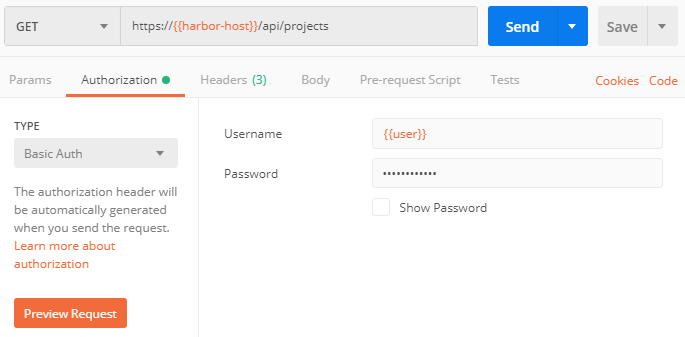
Most requests simply won’t work without authorization. The server response code “401 Unauthorized” will prompt you about the need for authorization.
List of repositories
The list of repositories in the project can be obtained through the search:
https://harbor.zabedu.ru/api/search?q=zabedu
This request returns information about the zabedu project and its repositories. You can also get the list of repositories in a separate list:
https://harbor.zabedu.ru/api/repositories?project_id=121
At the input, the request accepts the project id, you have already received the id above.
[
{
"id": 125,
"name": "zabedu/nginx",
"project_id": 121,
"description": "",
"pull_count": 0,
"star_count": 0,
"tags_count": 2,
"labels": [],
"creation_time": "2018-12-24T07:46:11.62455Z",
"update_time": "2018-12-24T07:46:11.62455Z"
},
{
"id": 126,
"name": "zabedu/mysql",
"project_id": 121,
"description": "",
"pull_count": 0,
"star_count": 0,
"tags_count": 1,
"labels": [],
"creation_time": "2018-12-24T07:53:44.408568Z",
"update_time": "2018-12-24T07:53:44.408568Z"
}
]
For a complete list of repositories, run the previous request without specifying the project name:
https://harbor.zabedu.ru/api/search?q=Tag List
You have a list of repositories, next tags are:
https://harbor.zabedu.ru/api/repositories/{{repo_name}}/tags[
{
"digest": "sha256:87e9b6904b42...4b53fdd467189f",
"name": "latest",
"size": 44698625,
"architecture": "amd64",
"os": "linux",
"docker_version": "17.06.2-ce",
"author": "as-NGINX",
"created": "2018-11-27T22:21:45.207738888Z",
"config": {
"labels": {
"maintainer": "as-NGINX"
}
},
"signature": null,
"scan_overview": {
"image_digest": "sha256:87e9b6...53fdd467189f",
"scan_status": "finished",
"job_id": 389,
"severity": 4,
"components": {
"total": 71,
"summary": [
{
"severity": 2,
"count": 1
},
{
"severity": 1,
"count": 66
},
{
"severity": 4,
"count": 4
}
]
},
"details_key": "d6bc3ea2...176d4be881d3",
"creation_time": "2018-12-24T07:46:11.661298Z",
"update_time": "2018-12-25T01:28:18.409452Z"
},
"labels": []
}
]
Name, signature, date of creation, size, architecture … Everything is there!
List of vulnerabilities
In the previous example, there is a “scan_overview” section in the data for each tag. This section contains information about the output of the clair vulnerability scanner:
- “Scan_status” – the result of the last scan;
- “Severity” – the maximum threat level for all detected vulnerabilities;
- “Summary” – the number of packets for each threat level;
- “Update_time” is the time of the last scan.
Need to prepare a summary report of the scan results? If there is not enough information about the number of detected vulnerabilities, you can get a complete detailed list of threats: Instead of: repo_name and: tag Postman will substitute the values of the corresponding variables.
https://harbor.zabedu.ru/api/repositories/:repo_name/tags/:tag/vulnerability/details[
{
"id": "CVE-2018-1152",
"severity": 3,
"package": "libjpeg-turbo",
"version": "1:1.5.1-2",
"description": "libjpeg-turbo 1.5.90 is vulnerable to a denial of service vulnerability caused by a divide by zero when processing a crafted BMP image.",
"link": "https://security-tracker.debian.org/tracker/CVE-2018-1152"
},
{
"id": "CVE-2017-15232",
"severity": 3,
"package": "libjpeg-turbo",
"version": "1:1.5.1-2",
"description": "libjpeg-turbo 1.5.2 has a NULL Pointer Dereference in jdpostct.c and jquant1.c via a crafted JPEG file.",
"link": "https://security-tracker.debian.org/tracker/CVE-2017-15232"
}
...
]
Viewing logs
Now you know what repositories and tags are in Harbor and what vulnerabilities have been found in them. It remains to be seen: who uploaded the vulnerability image to the registry?
https://harbor.zabedu.ru/api/logs?username={{username}}&repository={{repository}}&tag={{tag}}&operation={{operation}}&begin_timestamp={{begin_timestamp}}&end_timestamp={{end_timestamp}}&page={{page}}&page_size={{page_size}}Specify the search parameters you need, I left the repository name, tag and push operation:
[
{
"log_id": 1416,
"username": "as",
"project_id": 19,
"repo_name": "zabedu/nginx",
"repo_tag": "latest",
"guid": "",
"operation": "push",
"op_time": "2018-12-17T15:20:09.393893Z"
},
{
"log_id": 1412,
"username": "as",
"project_id": 19,
"repo_name": "zabedu/nginx",
"repo_tag": "latest",
"guid": "",
"operation": "push",
"op_time": "2018-12-17T14:47:03.151675Z"
}
...
]
This is enough to get familiar with the REST API Harbor. The REST API implements all of the Harbor management functions, not just getting information from the server. And don’t forget to share your successes!
Translated by Google Translate